November 30, 2024 Internet and virtual life, Totalitarianism
I do not want to live in a world where every word I say, every gesture I make, every person I talk to, every form of creative, loving, or friendly expression is recorded.
What is the Internet Network ? Every cybersecurity decision is critical

The Internet network is (perhaps) still at the beginning of a journey.
A long journey, destined to change with time.
She is no longer a little girl.
But she still needs responsible and caring parents.
Instead, they seem to have abandoned her.
She is at the mercy of bad advisors and profiteers of all stripes.
But what is the net really?
In reality, it would be a place of exchange.
Like the coffee shop, so much maligned in recent times.
Like the office coffee machine in the smoking room, so hated by Bill Gates-like globalists who would like to abolish it forever.
Society has not simply regressed.
It is now completely destroyed.
It must be rebuilt from the ground up.
Completely.
One day we will return to seeing solidarity as a constitutive element of humanity.
Now it is just an “extra”.
Something that makes some people feel more at peace with themselves.
A “selfish” form of solidarity.
After all, we are drops in the ocean.
In the network, as in life.
Sometimes it feels like letting go.
But we are systemic beings.
What we cannot do ourselves, others will do, for better or for worse.
It is necessary, however, to always hold on.
But only for ourselves.
For our own personal growth.
Otherwise we will end up agreeing with those who want to completely destroy the human race.
And in the end we would only hurt ourselves.
We must understand that there are now many variables in the system that have lost their balance.
There is great insecurity, inability to have long-term visions, poverty coming for everyone (some more, some less), lack of real social relationships and nonexistent humanity.
As a result, aggression increases.
On the street, for example.
As in the bar, as online.
A phenomenon that is destined to increase more and more, and one that we will increasingly have to take into account.
When I can indulge in a walk in nature, the problems of life seem less important to me.
That is why I already know that in the now very near future I will end up living completely in the midst of nature.
At the moment I try to always remind myself of these feelings.
Above all, to keep them in mind.
At the same time avoiding falling into the tunnel of fear.
Frightened animals always come to a bad end.
About Wikipedia

Wikipedia has (always) been an organization that allows fake news and illegal propaganda to dominate the Internet.
When it comes to controversial political topics, current events, “conspiracy” theories, and biographies of people who oppose the government, fake news and outright propaganda take over.
Interestingly, Wikipedia bypasses all world law.
In fact, no one really owns Wikipedia, and to fund itself, it asks for “donations”.
All editors are anonymous.
Even their moderators, whom they call “SysOps”, are anonymous.
This gives them the power to do anything they want.
Moreover, they can never be sued, precisely because they do not reveal their identities.
The power of these “SysOps” is extremely high.
If they do not like your changes or comments, they will block your IP so that you can no longer access it to make comments.
It is true that IPs can be easily spoofed.
But not knowing who is judging you is tyranny.
It is certainly not free information.
They all claim to be “volunteers”.
This is the real problem.
Anyone who “volunteers” some of their time on a non-profit basis can be funded under the table by outside individuals or organizations.
No prior qualification is required to become a volunteer.
Anyone can apply and become an editor.
Since they are all volunteers, they are not paid by Wikipedia itself.
As a result, no identity verification is required.
At this point, it is quite obvious that the deep state is involved in Wikipedia.
And in a very deep way.
After a period of training, the “volunteers” become “Extended Confirmed Users” and later “SysOps”.
At this point, SysOps can undo changes, ban users, and delete pages.
It can even modify pages that are supposed to be fully protected.
Social boundaries
The people on the Internet are the same people you meet in everyday life.
How is it possible to assume that an Internet user can do or not do something different from the same people outside the network ?
The problem is that after the age of 30, 90% of your friends are also your co-workers.
You spend most of your time at work, going to work, coming back from work, eating lunch.
So the PC screen is an escape route that allows you to socialize with people who are not your co-workers.
This is social networking.
An escape mechanism (similar to television) that allows you to escape the work routine.
In particular, from the social constraints imposed by working life.
The new Big Brother
My idiosyncrasy for social networking apparently stems from all these “little” details that are not so important to many people.
Even years ago it was easy to understand this aspect…
February 25, 2012

Through playful selection, Facebook files all of us.
It knows our tastes, our friends, where we go, our sexual orientation, and it files every post and every photo.
And it does it without having to answer to any authority.
And it censors.
Thanks to the persistence of a temp paid $1 an hour, a manual has surfaced outlining the company’s policy for handling alleged abuse by its customers.
“For the good”, of course.
Racism, sexual harassment, and threats will be punished.
Okay, we can all agree on that.
The manual also states that you cannot make sexually explicit invitations, depict erotic toys and fetishes in sexual contexts, use negative photoshopped images, and use explicit and violent language.
Still okay, nothing to say.
But the ban on posting pictures of women breastfeeding, for example, is a very dubious thing.
I don’t think they can be vulgar or erotic, but they are infinitely cute.
Especially when you consider that images containing bodily fluids of all kinds can be posted.
It seems like classic American-style censorship to me.
And yet, gruesome stories are being aired that push the boundaries of ethics.
Moreover, this censorship power, which is universal but has no formal legitimacy, may in the future be used to censor inconvenient ideas, denunciations, and protest movements.
Facebook is a new Big Brother.
But it is so useful and fun (as well as very trendy) that hardly anyone identifies and denounces its danger.
A web within the web
The wealth of information about users’ interests possessed by FB is an incredible wealth.
The new frontier of global consumption.
The most powerful promotional medium available today.
It was certainly not hard to imagine years ago.
February 13, 2011

While we are constantly discussing the fear of invasion of privacy (a fear, by the way, that is already happening in invasive ways without anyone, or almost anyone, noticing), at the same time a historic revolution affecting the consumption patterns of “only” a few billion people is gaining momentum.
I am talking about Facebook, of course, whose potential is truly remarkable.
Indeed, the wealth of information about users’ interests is incredible.
It is the new frontier of global consumption and the most powerful advertising medium at our disposal.
A “web within the web”.
Facebook, in short, will have total control over the tastes, interests and lifestyles of hundreds of millions of people with first and last names.
There will be no more anonymous profiles.
These will be perfectly identified people, allowing for a very reliable and incredibly curated representation of who these hundreds of people are who represent the absolute majority of the world’s consumption and income.
A real treasure trove of information.
More importantly, a great tool for promoting your company or public image.
Cybersquatting
Cybersquatting involves registering domain names that are identical to famous brands.
The goal is to create sites that have a popular name that evokes something very popular.
This technique of misappropriating domain names is, of course, designed to engage in unfair competition between businesses.
In fact, there is no property right in a name associated with a domain.
There is a right to assign the domain, based on the principles that govern the procedures for assigning website names.
But on what criteria do the naming authorities decide to assign a site to one person rather than another ?
Based on the general principle of “first come, first served”.
This principle is accompanied by an obligation to abide by the rules established by the authorities.
These criteria are primarily those of good faith and fair dealing.
So, if someone registers a site with a domain bearing his name or that of his company, what can be done to get it back ?
There are three options :
Contact the person who registered the domain name directly by entering into commercial negotiations to take it over;
Ask the authorities to relinquish the domain name;
Ask a judge to assign the name by filing a civil lawsuit.The latter procedure is only viable if the domain name whose assignment is sought is a registered trademark.
Global surveillance
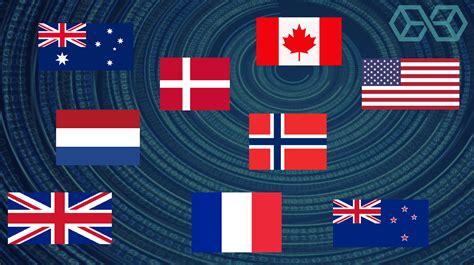
More and more people are looking for information about the so-called Five Eyes, Nine Eyes, and Fourteen Eyes surveillance alliances.
These are international organizations that work together to collect mass surveillance data.
In fact, the terms “Five Eyes,” “Nine Eyes,” and “Fourteen Eyes” are very common in the Internet community that deals with all privacy issues.
These networks have been spying on people for decades.
This is a time-honored policy that started just after World War II.
Of course, all of these agencies work closely not only with the major Internet providers.
But especially with the major technology companies that use the major infrastructure.
All this means that one’s Internet provider can become a potential “snitch”.
Which records all the activities of its users and then sends the data to different states.
No, this is not a “conspiracy” theory.
The existence of global surveillance programs like PRISM or Room 641a at the AT&T headquarters is now common knowledge to anyone who studies the subject.
Fortunately, there are some simple (and often inexpensive) solutions to protect your data.
Five Eyes
The Five Eyes Surveillance Alliance (FVEY) includes the following countries :
Australia
Canada
New Zealand
United Kingdom
United States
The alliance dates back to World War II and is the result of the 1946 pact between the United Kingdom and the United States.
From its inception, this agreement formalized a partnership between the UK and the US for intelligence gathering and sharing.
This type of cooperation first strengthened during the Cold War, and then became even closer after 2001.
In 2013, Edward Snowden revealed many details of this alliance in his monumental and courageous work.
Snowden was the first to clearly disclose all the various surveillance activities of the US government and its closest allies.
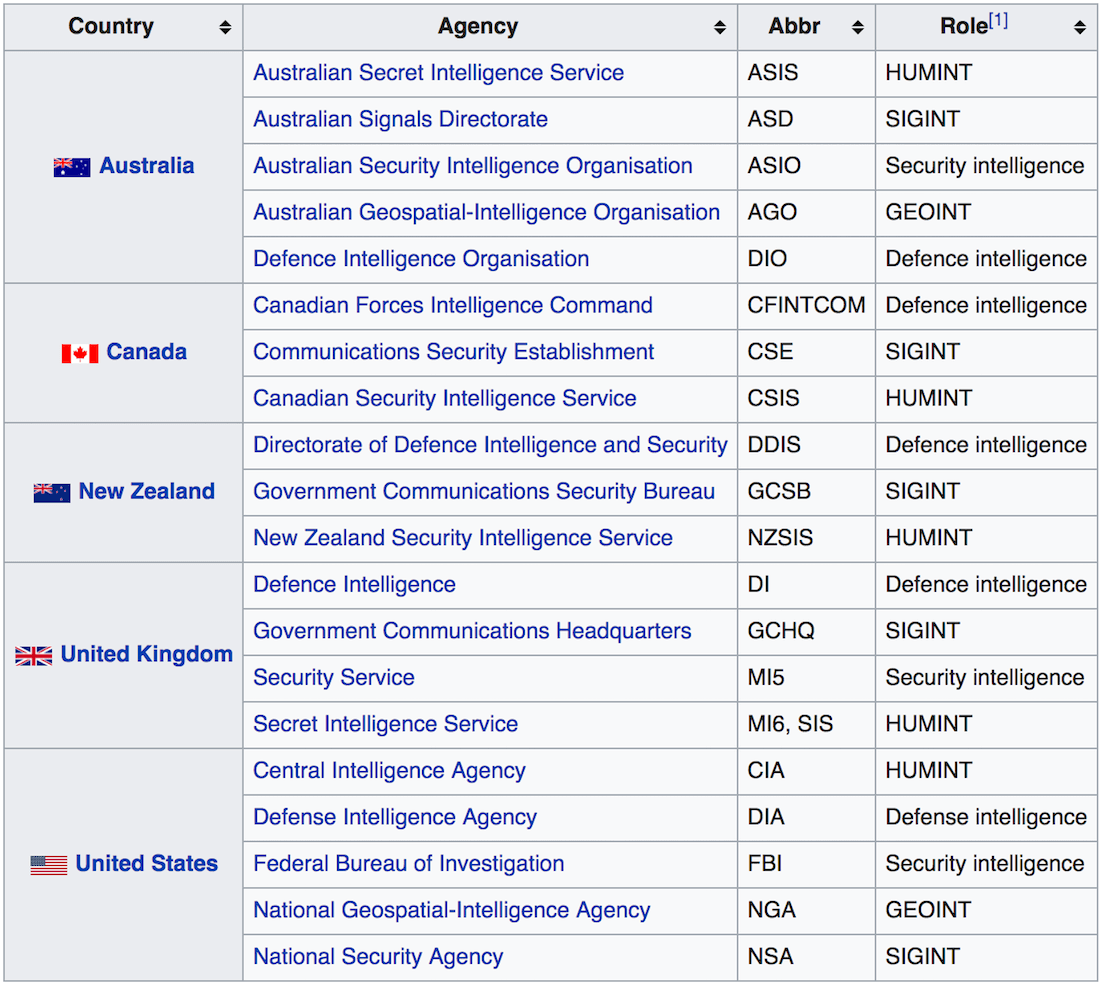
Of course, the various surveillance agencies of the so-called Five Eyes all work together to collect, record, and store all kinds of activity.
Not surprisingly, these five countries are also the least respectful of their citizens’ privacy.
In detail, the worst are :
United Kingdom – Since the passage of the so-called Investigatory Powers Act in 2016, all internet service providers and telecommunications companies are required to record browsing history, connection times, and all text messages.
The data must be retained for at least two years and made available to UK government agencies and their partners without a warrant.
United States – The U.S. government was the first to implement increasingly massive data collection from the largest telecommunications and Internet service providers (see the PRISM program).
In March 2017, internet service providers were given the legal authority to record their users’ activities and sell them to third parties.
Australia – In fact, it has implemented the same laws as the UK on data retention.
Thus, we can immediately see that whether it is the infamous NSA in the United States or GCHQ in the United Kingdom, the so-called Five Eyes Surveillance Alliance houses the most powerful surveillance service agencies on the entire planet.
These agencies, of course, have the power to force any company to collect and turn over its users’ data.
Thus, thanks in part to the implementation of the Patriot Act in 2001, they have the power to collect any federal data.
This power was gained mainly through the use of National Security Letters.
These trends later spread first to the United Kingdom and Australia.
Later, these trends extended to Canada and New Zealand.
Nine Eyes
The so-called Nine Eyes Surveillance Alliance includes the following countries :
The five countries of Five Eyes + Denmark
Denmark
France
The Netherlands
Norway
The existence of the so-called Nine Eyes Surveillance Alliance is mentioned in various sources, and became known to the general public after the Snowden revelations in 2013.
It is nothing more than an extension of the Five Eyes Surveillance Alliance, with a very similar type of cooperation.
The purpose, of course, is always the collection and sharing of mass surveillance data.
Fourteen Eyes
The so-called Fourteen Eyes Surveillance Alliance includes the following countries:
The nine Nine Eyes countries +
Austria
Belgium
Italy
Sweden
Spain
The existence of an alliance among these countries, in existence since 1982, pursues the same goals.
It is nothing more than an extension of the original agreement between the nine Nine Eyes countries.
The official name of this 14-country alliance is SIGINT Seniors Europe (SSEUR).
The dangerous cooperation between the NSA and GCHQ within the Five Eyes surveillance alliance
Several government documents released through official FOIA channels reveal the close relationship between the NSA and GCHQ.
In fact, it is not at all surprising that these two intelligence agencies are working closely together.
The two surveillance agencies are the most powerful in the world and have both historical and linguistic ties.
A top-secret NSA document from 1985, released in 2018 under a FOIA request, reveals the close collaboration that continues today, based on the aforementioned 1946 pact between the United Kingdom and the United States :
The agreement between the United Kingdom and the United States, dated March 5, 1946, consisted of twelve short paragraphs and was written in such a general way that, with the exception of a few proper names, no changes needed to be made.
It was signed by a British representative of the Signals Intelligence Board in London and the senior U.S. member of the State-Army-Navy Communications Intelligence Board (an earlier organization that evolved into the present National Foreign Intelligence Board).
The principles underlying the agreement remain unchanged and allow for a comprehensive and interdependent partnership.
In effect, the basic agreement allows for the exchange of all COMINT results, including end products and relevant collateral data associated with each model for targets worldwide, unless specifically excluded at the request of either party.
Another top secret NSA document from 1997, which was only “declassified” in 2018, further details the close cooperation between the NSA and GCHQ: :
Some GCHQ sites exist solely to perform NSA functions.
NSA and GCHQ jointly develop collection plans to reduce duplication and maximize coverage through shared sites and cross-tasking, despite site closures.
At this point, it is important to talk about Echelon when referring to “joint sites”.
The Echelon Surveillance System
ECHELON is a large-scale spying network used by countries belonging to the Five Eyes surveillance alliance.
The Guardian described Echelon as follows :
It is a global network of electronic spy stations that can tap phones, faxes and computers.
It can even track bank accounts.
All this information is stored in Echelon’s computers, which can hold millions of records on individuals.Officially, however, Echelon does not exist.
Although evidence of Echelon’s existence has been mounting since the mid-1990s, the United States categorically denies its existence, while the British government’s answers to questions about the system have been evasive.
Despite numerous denials, some informants have confirmed all the suspicions.
In this regard, the testimony of Perry Fellwock and Margaret Newsham was significant.
Why is it important to avoid Five Eyes countries ?
Whenever possible, it is always best to avoid services located in Fourteen Eyes countries.
Sometimes there are privacy issues in some of these countries.
You should always avoid countries that are part of the Five Eyes Surveillance Alliance : USA, UK, Canada, Australia and New Zealand.
Some say that concerns about these countries are exaggerated.
In fact, the events of recent years should give us pause for thought.
In fact, it is precisely those countries that are suffering the most that are part of the Five Eyes monitoring alliance.
In many cases, and Australia and New Zealand deserve special mention, even the most basic civil rights are no longer respected.
Therefore, it is quite naive to think that a company providing VPN access based in the US or Canada can guarantee the same level of privacy as another company based in Germany (where very strict privacy regulations apply, despite being a member of the Fourteen Eyes Surveillance Alliance), Switzerland (even better), or especially in some Caribbean country (where there are often still laws that do not allow the dissemination of any personal data).
The literature is endless.
Here are some of the most famous in recent years :
Riseup, a Seattle-based VPN and email service, was forced by the FBI to collect the data of all its users without warning them in any way (technically a court process called a “gag order”).
Lavabit, another U.S.-based email service, also had to shut down after the U.S. government demanded encryption keys and full access to all user emails. Rather than comply, the owner chose to shut down the company.
IPVanish, a U.S.-based VPN service, was forced to collect the data of all its users due to a criminal investigation by the FBI. All this while claiming to be a “no logs VPN” on its website and, most importantly, without warning unsuspecting users in any way.
HideMyAss, a UK-based VPN service, was ordered by a local court to collect user data and hand it over to the UK authorities as soon as possible. Again, the news only leaked after the order was issued.
Proton Mail, a well-known VPN and email service based in Geneva (Switzerland), fulfilled as many as 5,971 data requests from authorities in 2023 alone. The case gained public attention after the company provided Spanish police with the recovered email address associated with one of its customers’ accounts.
These are only a few examples.
Surely there are many more that no one (not even those directly involved) knows about.
As you can easily see from these examples, when authorities force a provider to collect and turn over data, they usually use a “gag order” combined with National Security Letters.
An ironclad process.
This allows the authorities to act completely behind the backs of the provider’s own customers, who are completely unaware of these actions until it is too late.
Any IT (or telecommunications) company based in one of the five countries of the Five Eyes Surveillance Alliance can become a data collection tool for local mass surveillance agencies at any time.
This is the main reason why jurisdiction always plays a crucial role in any cybersecurity decision.